
About AWS GuardDuty
Amazon GuardDuty is a region-based, intelligent threat detection service that allows users to monitor their AWS accounts for unusual and unintended behaviors by analyzing AWS CloudTrail event logs, VPC flow logs and DNS logs. It then uses the data from these logs and evaluates them against multiple security incidents and threat detection feeds, looking for anomalies and known malicious sources such as IP addresses and URLs.
How does GuardDuty Work?
Amazon GuardDuty is powered by Machine Learning which advantageously enables GuardDuty to continuously evolve by learning and understanding operational behaviors within the AWS cloud infrastructure. Once GuardDuty receives the data, it looks for abnormal patterns within the AWS infrastructure which could cause/indicate potential threats to the AWS environment. These threats could be behavioral based, where a resource has been compromised by an accidental account or credential exposure. This fires unexpected API calls which are usually considered outside security best practices. GuardDuty also monitors and reports communications from suspicious sources.
Why GuardDuty
AWS still treats security as its number one priority across its public cloud. They know that without adequate security techniques, mechanisms and measures in place to safeguard and protect their customers and their data, their customers will not have the confidence to use their services. Cloud security can still be seen as one of the main reasons that companies are slow to adopt cloud technology from a public cloud provider such as AWS. GuardDuty uses rule sets created by AWS from information collected by the AWS Security teams, third party intelligence partners, other anomaly detection sources, and Machine Learning technology to identify potentially malicious activities. Once these events are found, they can also be integrated into other workflows such as AWS Lambda for automated remediation and prevention.
Enabling GuardDuty
Like other AWS services, GuardDuty can easily be activated through the AWS console. Once activated, it starts monitoring all the resources in your account within no time.
Step 1: Login to AWS console. Type “GuardDuty” in the search bar under the Services dropdown. Click to open GuardDuty.
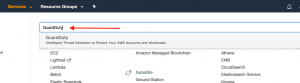
Step 2: You will be greeted by the GuardDuty welcome page. Click on Get Started. 
Step 3: Once you’re in, you will be asked to enable GuardDuty. The system will also create an IAM service role which will have read access to Ec2 describe and images. You can view the Policy by clicking the View option.
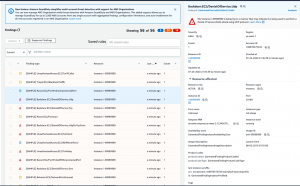
Once enabled, GuardDuty will start monitoring the account and resources. GuardDuty analyzes VPC Flow logs, CloudTrail logs and DNS logs. Once GuardDuty is operational, its Machine Learning module will start learning/monitoring the account and start to report any findings in the Findings view on the console. The below screenshots were taken from our sample findings generated by AWS for your understanding. Once you click on any finding, you will be given a detailed summary of the incident.
Pricing
When you first enable GuardDuty, you will get a 30-day free trial. After that, charges are based upon the amount of traffic in the log files and infrastructure loads. Please refer here for more details on pricing.






